Scammers use phishing to trick you into disclosing sensitive information, such as credit card numbers, passwords, Social Security numbers, or banking details. To establish trust, phishers impersonate a trustworthy person, a popular website, a government agency, or a bank.
In today’s digital warfare, phishing scams have become a global cybersecurity challenge. The FBI’s Internet Crime Complaint Center (IC3) Report revealed that approximately 300,000 phishing incidents occurred in 2023.
Microsoft also considers phishing one of the most significant cybercrimes. According to Mika Aalto, co-founder and CEO of Hoxhunt, “In the near future, AI will power significantly more phishing attacks—everything from text-based impersonations to deepfake communications will become cheaper, more convincing, and more popular with threat actors.”
In a phishing email, a fraudulent message is crafted to look authentic. It may ask you to click on a suspicious link or open an infected attachment to install malware on your computer. Moreover, phishing emails create a sense of urgency, fear, and uncertainty. They employ high-pressure tactics to coerce you into acting quickly.
With how advanced these schemes have gotten over the years, it’s no longer enough to simply try to prevent an attack. Anyone can be targeted by these schemes, and people from all digital literacy backgrounds have fallen victim. Consequently, it’s crucial that you know what to do after a phishing scam, so read on to learn more.
Figure 1: Locked Account Phishing Example
(Source: Trend Micro)
Step 1: Stay Calm and Assess the Situation
If you have become a victim of a phishing attack, don’t panic. Instead, take a moment to assess the situation carefully. Hastiness can further worsen the problem. You must respond rationally to minimize potential damage.
First and foremost, stop interacting with scammers and avoid providing any sensitive information. These fraudsters aim to trick you into revealing personal information, making their attack more persuasive and dangerous.
If you have opened a link or attachment in a phishing email, the malware may have been installed on your machine. But don’t panic — here’s what to do after clicking on a phishing link.
Under such circumstances, you need to check your laptop or computer behavior. Unnecessary or unwanted pop-ups may indicate an attack. Viruses often slow down your machine and severely affect application performance.
Step 2: Verify the Sender
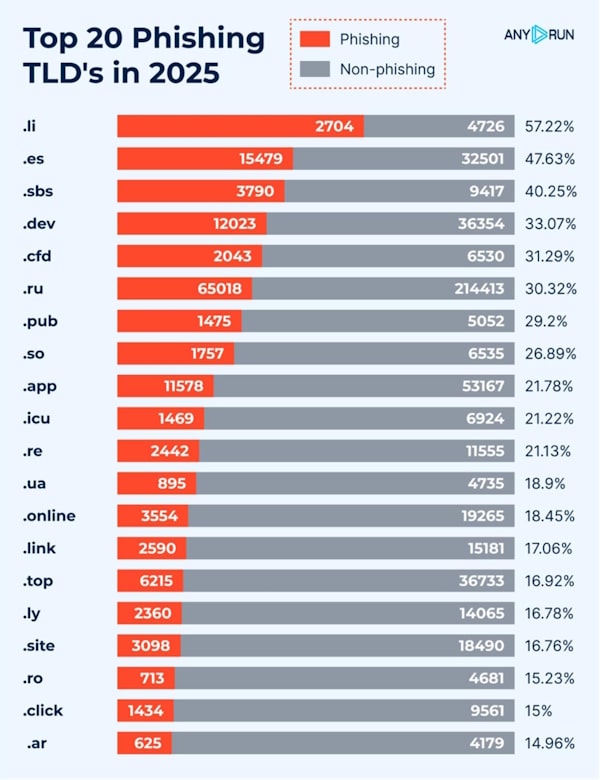
You must closely assess the sender’s email address or phone number. In most cases, scammers use free domains. Scam Wave provides a verified list of some of these fraudulent websites. According to 2025’s data from ANY.RUN, the .li domain is ranked first in phishing abuse by ratio. Furthermore, 57% of identified .li domains were malicious.
(Source: Hack Read)
Moreover, phishing emails may include spelling mistakes. For example, www.google.com can be mimicked by replacing the lowercase “l” with an uppercase “I.” This results in a phishing domain that reads as www.googIe.com.
If the sender claims to be a company or a law enforcement officer, go directly to official websites or dial phone numbers to verify authenticity. The phisher’s email address will be slightly different from the official address of an honest company.
Step 3: Disconnect and Secure Your Device
You should disconnect your device from the internet to prevent phishers from accessing or encrypting your data. Ensure that you have turned off all types of internet connections, including:
- Ethernet cable
- Mobile data
- Wi-Fi
This process will stop ongoing data transmission and reduce the risk of further malware propagation. But what if you opened the phishing link on your mobile device instead of a computer? Fear not, for our experts know exactly what to do after clicking a phishing link on an iPhone.
First, turn on airplane mode to disconnect the phone from the internet. If necessary, erase all data or apply a factory reset. After that, restore your device from an iCloud backup. After this, you should proceed with the options discussed in the subsequent sections.
Step 4: Run a Full Security Scan
This involves running a full system scan with a built-in or third-party security tool. For Windows operating systems, you can use Microsoft Windows Defender. Make sure your software is up to date.
Likewise, if you use a third-party security suite, ensure that it’s patched and up to date. A complete system scan will help detect the intrusion, quarantine the infection, and eliminate or neutralize the threat. The third-party security tool should come from a reputable provider.
You can seek the services of a professional digital forensics service if the attack is persistent. This will help identify the root cause of the threat, preserve the evidence, and minimize potential damage.
Step 5: Change Your Passwords Immediately
Maintaining good password hygiene is essential to enhancing your online privacy and security. After confirming a phishing attack, you should change all your critical passwords immediately. If you use a common password for multiple accounts, it can lead to serious consequences.
A strong password is the first line of defense in cybersecurity. When changing your password, ensure you choose a unique, strong one. Avoid choosing easy passwords like “1234” or “0000.” According to Ryan Galluzzo, a leader of NIST’s Digital Identity Program, “The worst password I can think of is ‘password’ or ‘12345’.”
You must create a strong password that consists of letters, numbers, uppercase and lowercase letters, and symbols.
Additionally, you should set up a passkey or Multi-Factor Authentication (MFA) for all your accounts to boost security. Doing so ensures that even if a scammer gains access to your password, they’ll still need to bypass an extra security step.
Phishing attacks often target individuals who are less tech-savvy, such as senior citizens. If an elderly family member has fallen for a phishing scam, help them change all crucial passwords immediately and report phishing scams.


Step 6: Secure Your Online Accounts (Including Facebook and Instagram)
If you are sure that you have fallen prey to a phishing attack, secure all of your online accounts. First and foremost, you must pay careful attention to your banking accounts. Your bank statement will inform you whether someone has made a suspicious transaction. If you discover any malicious activities, you should immediately report them to your relevant bank.
The inbox of your email account may include a suspicious email that requests personal information or links to infected websites. If you receive any message that causes you to take pause, you can confirm its legitimacy by reaching out to the supposed sender through a verified contact method. You can typically find this information on the “contact us” page on their official website.
You might be asking what to do after a phishing attack on Facebook, or how to recover an Instagram account after a phishing attack. First, you need to report your compromised account, regardless of whether you can log in to it. According to Facebook, you should take the following steps to recover your account:
- Reset your password.
- Remove any unauthorized devices or logins that have signed into your account.
- Review ‘activity log’ and Facebook Feed to identify and remove any unfamiliar posts.
- Check recent emails sent by Facebook.
Additionally, many online platforms, such as Facebook, Instagram, and Reddit, store login history within activity logs. This data includes IP addresses and the account’s location. You can use this information to identify unfamiliar activity or logins during odd hours.
Step 7: Alert Financial Institutions
If a phishing attack tricked you into entering banking information, here’s what you should do. First, you should contact your credit card company or bank immediately. The bank will freeze your bank account, cancel your compromised credit or debit card, and enable fraud alerts.
Sometimes, threat actors verify the transaction by sending a One-Time Password (OTP) to your registered phone number and then calling to ask for it. They pretend to be legitimate people and convince you to recite an OTP. Under such circumstances, you must not share an OTP with any other person. Change your password immediately after the incident.
Step 8: Protect Yourself from Future Phishing Attacks
Addressing the current data breach isn’t enough on its own. The wise approach is to learn from past lessons and strengthen your security posture for the future. To prevent or foil phishing attacks, our experts suggest you adhere to the following guidelines.
- Don’t open a message from unfamiliar senders. Email headers of these emails may include deceptively worded email addresses or sender names. The body may reveal links and attachments that camouflage infected code.
- Try to remain calm. The panic-inducing message can impair your critical thinking, leading you to make ill-informed, rash, or hasty decisions. If you find any suspicious messages, inform your boss or manager.
- Avoid sharing personal and sensitive information, such as passwords, social security numbers, and banking details — even with a trusted individual.
- Block spam emails using reliable spam filters. Most email clients already include built-in spam filtering tools. However, you can still leverage powerful third-party spam filters.
- Use a Secure Web Gateway (SWG) to filter malicious traffic. SWG analyzes network traffic and blocks incoming requests as per the predetermined security policies.
- Utilize a browser isolation service to avoid clicking on a malicious link or attachment. Fraudsters deliver these infections via a web-based email client.
- Use email security protocols to prevent domain spoofing attacks. Always verify the source of an email by leveraging email authentication methods, including:
- Sender Policy Framework (SPF)
- DomainKeys Identified Mail (DKIM)
- Domain-based Message Authentication Reporting and Conformance (DMARC)
- Use Multifactor Authentication (MFA) to add a layer of security to your account. MFA helps prevent phishing scams even if your password has been compromised.
- Don’t make financial transactions on public Wi-Fi, such as restaurants, hotels, or airports.
- Regularly update your operating system and application programs, especially your security suite. Always use an official and patched operating system and programs.
- Be vigilant and educated through cybersecurity training and awareness programs. If you are a company, ensure that periodic training is provided for employees.
Example: the “Robust Phishing Awareness Training That Validates Learning and Changes Behavior” by SANS Institute. - Organizations should encourage a reporting culture in which employees can comfortably report suspicious emails without fear of blame. Deploy secure email gateways to detect and block phishing attacks before they reach your employees.
FAQs
What happens if I click on a phishing link?
When you click on a phishing link, it will redirect you to a malicious web page or lure you into downloading a harmful attachment. Any hasty decision may result in passwords being stolen and data being breached.
How do I recover my account after a phishing attack?
If you have been phished, change your password, enable MFA, scan for malware, report the incident, and flag any unauthorized transactions.
What should elderly victims of phishing do first?
The FBI has already warned that older Americans suffer the most significant level of financial losses due to digital crimes. If you have become a victim, disconnect from the internet and report the incident to your law enforcement agency. Get help from your email providers and recover all accounts.
Should I reset my phone after opening a phishing email?
You can consider resetting your phone, but you should only take this step if it’s necessary. For example, you can take this action if you have been assured that the malware has been installed and not removed. It’s important to note that while resetting the phone can remove malware, it can also delete critical evidence. Be sure to conduct a proper investigation to ensure the evidence is preserved.







