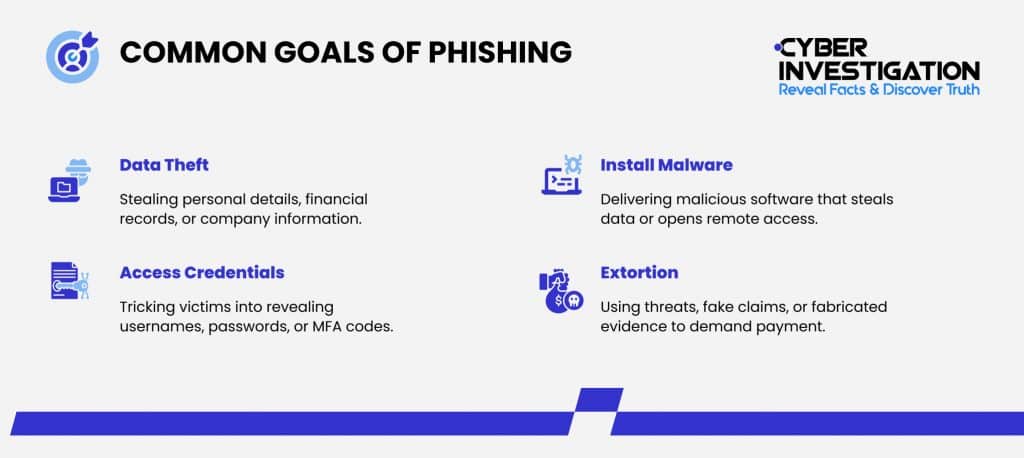
The Most Common Signs of Phishing Scams
Knowing how to spot phishing scams starts with understanding the red flags that keep reappearing. Even though today’s attackers utilize polished words and better-looking products, the basic deceits remain unchanged. This checklist emphasizes the most common signs of phishing scams and helps you take a moment before you respond.
- Incorrect spelling or grammar. However, scammers increasingly utilize AI tools which make their text grammatically correct and more refined.
- Unknown or unexpected sender address or mismatched domains, particularly when the email is purported to be from a large company or a bank.
- Use of a very urgent or pressing tone that tries to make you act without thinking or to get you to reply rapidly, saying things like “Act now,” or “Verify your account.”
- Requests for sensitive information like passwords, banking data, or codes. Remember that legitimate companies never do this through email or text.
- Questions that make you feel like you must respond immediately without even thinking about it, along with links or files that work towards this goal. Usually, they are disguised as invoices, delivery updates, or security notices.
- Phony security notifications or blackmail threats created to intimidate recipients to react without verifying the source.
- Branding inconsistencies — such as mismatched logos, colors, or formatting — can help you identify that the communication may not be from the original source.
- Requests for cryptocurrency, prepaid cards, or gift cards are almost always fraud signs since these are untraceable and cannot be reversed.
One cannot underestimate how crucial it is to identify these red flags as soon as possible. Even if you see a message that appears grammatically perfect and professional, slow down and check for these red flags.
How to Identify Phishing Scams in the Age of AI
Knowing how to identify phishing scams is essential nowadays, especially after the introduction of AI tools that make fraudulently generated messages appear legitimate. Offenders can now program an email in the best grammatical style, use branding templates, and even sign off in a most realistic way.
Besides, videos created with AI and calls made with fake voices can sound as if the CEO of the company, a colleague, or a member of the family is talking to you, thus making many victims unable to detect the scam.
As a first step to your safety, start by manually verifying the sender.
- Character by character, look through the domain to identify any discrepancies since many deceits use similar domains.
- Before clicking any link, check it by hovering over it. If the link leads to a certain website, compare it with the actual one. This ensures that you are going to the real site.
- Confirm whatever requests you receive by using another means of communication coming from a familiar phone number or official support email.
Moreover, employing security measures might be an excellent idea.
- Anti-phishing browser extensions can help by blocking harmful sites and warning you about suspicious downloads. They do not allow visiting of harmful sites and give a warning in case of suspicious downloads.
- Highly sophisticated spam filters are capable of identifying even the most minute unusual email patterns that exist in the account. Thus, they are able to do this even when emails are very professional.
- Deepfake-detection tools are not that far away from being universally adopted. They may give you a hand in detecting voice or video manipulations for strange requests.
Knowing how to stop AI-generated phishing scams means pairing good habits with modern defenses. AI may play a role in enabling criminals to come up with plausible but fraudulent messages. However, the same technology is also used in the creation of security systems which help identify AI-generated speech, fake images, or detect behavioral patterns that point to threats.
How to Avoid and Prevent Phishing Scams
Learning how to avoid phishing scams starts with building strong digital habits that protect you before a scam ever reaches your inbox. Phishers rely on situations where the victim reacts quickly and has weak security settings. Thus, small changes in your daily routine are enough to put most threats at bay. These habits are effective for individuals, families, and organizations of any size.
Strengthening your account security can be a good first step.
- Do not reuse passwords under any circumstances and use a password manager to keep everything neat and safe.
- Put multi-factor authentication (MFA) on as many accounts as possible so that a password alone will not be sufficient for the attacker.
- Make sure software, apps, and browsers are all up to date, as updates are generally accompanied by security patches that prevent new phishing methods.
Employee awareness is equally important for a business.
- Empower employees with frequent training on phishing, such as identifying and promptly reporting suspicious emails.
- Confirm all payment or data requests, especially if they are related to wire transfers, login resets, or sensitive documents.
- Use internal communication rules, such as direct conversations to confirm a major transaction or an unanticipated request from executives.
Pro Tip: If a message makes you panic, it might be a forgery. Scammers utilize fear and urgency to get their targets to react immediately. Pausing for even a few seconds can be enough to dismantle the entire strategy.
Knowing how to prevent phishing scams is not necessarily through technical acumen, but rather by slowing down, confirming the messages, and employing the use of security tools.