Founded in 2003, Skype was a communications platform that was known for voice and video calls. The platform was then discontinued in favor of Microsoft Teams in 2025. Many users were concerned about scams and how to stop blackmail on Skype when it was active. Today, those same concerns apply to Microsoft Teams. You should always remain cautious of scammers online. Cybercriminals are looking to exploit any online platform, and that includes Microsoft Teams. The moment you let your guard down is when criminals take advantage.
The Difference Between Skype and Microsoft Teams
Skype was made for individuals and small groups to connect over voice or video calls. The platform also had instant messaging capabilities. It was primarily for personal use, and scammers would exploit it by luring victims to the platform to continue their schemes like sextortion or romance scams.
On the other hand, Microsoft Teams was created to be a hub for workplace communication. Businesses and organizations rely on Teams to communicate through chats, video meetings, file sharing, and project management. Communication typically remains within an organization on Teams, greatly reducing the chances of bad actors gaining unauthorized access. However, just like with any online platform, there are vulnerabilities in Teams that cybercriminals can use to infiltrate organizations.

What Does Blackmail Look Like on Microsoft Teams?
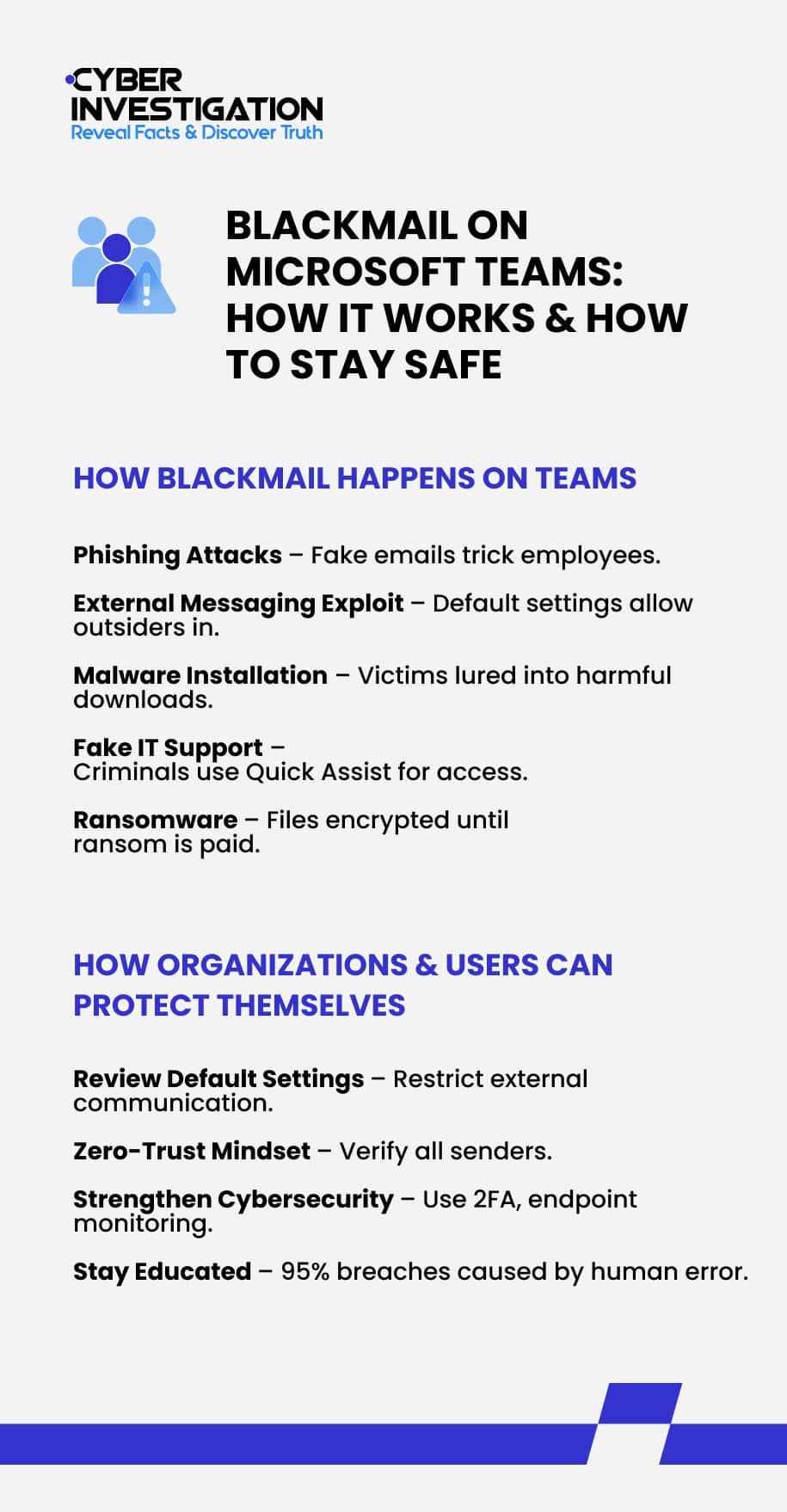
Cybercriminals on Teams are typically targeting businesses and organizations and rely on ransomware for blackmail. They use multi-stage phishing tactics to trick employees into giving them access and then steal data for blackmail.
It’s also common for blackmailers to exploit the Microsoft Teams setting that allows external users to message those in an internal communication network. This is a default configuration that organizations must change manually when using Teams. However, many do not.
This opens the door for bad actors to message organization members or employees and trick them into performing a harmful act. It’s common for cybercriminals to lure victims on Teams into installing malicious software or providing remote access to their computer. From there, the perpetrator looks to infiltrate the company network and hold files for ransom.
In one example, a blackmailer posing as IT support tricked a business employee into providing them remote access to their computer with Microsoft Quick Assist. This is a built-in Windows tool that allows other people to monitor your activity on your device or take over the computer entirely. With control over the victim’s computer, the criminal can gain access to a corporation’s files and deploy ransomware for blackmail.
Ransomware is a form of malicious software that encrypts data until a ransom is paid. It remains one of the most widespread cyberattacks globally, with perpetrators receiving over one billion dollars in payments in 2023 alone.
Other forms of Blackmail on Teams
While users primarily use Teams for professional communication, Microsoft is also encouraging that the app is used personally. Similar to Skype, Microsoft wants people to look at Teams as a tool to connect with family and friends online.
However, personal use creates different security risks. In some cases, it may create an opportunity for bad actors to exploit sensitive information and blackmail users. Sextortion can also become a huge issue on Teams with video calls and multimedia messages intertwined with the platform.
How to Stop Blackmail on Microsoft Teams
Whether the question is how to stop blackmail on Skype or Microsoft Teams, how you respond to the incident is an important determinant in how the situation will end. It’s essential to keep a cool head and to have a plan to resolve and mitigate the damage of the event quickly. Take note of the following steps when you need to deal with blackmail as an individual or organization.
Do Not Ever Comply with a Blackmailer’s Demands
Cybercriminals want victims to believe that compliance is their most viable option. However, giving in to a blackmailer’s demands only empowers them to continue targeting you because you are susceptible to their tactics. It also communicates that you are willing to meet their demands to protect your privacy which gives them more leverage over you.
Preserve the Evidence
It’s vital to document, track, and preserve the evidence of the blackmail. This should include the identification of the attack vector and point of entry for the criminal in an organization or business. For personal matters, you should screenshot messages, profiles involved, and anything else that is relevant to the crime.
Businesses Must Have an Incident Response Plan
An incident response plan is a proactive strategy formed by organizations to deal with cyberattacks. The plan helps businesses establish procedures for detecting, responding to, and recovering from cybersecurity incidents efficiently. It also reduces the number of data breaches by strengthening employee training and cybersecurity practices.
Incident response plans typically have six different phases: preparation, identification, containment, eradication, recovery, and lessons learned. Each phase moves toward the goal of removing the threat and returning business operations to the status quo efficiently. The longer business operations are down, the more money it costs overall.
Report Blackmail to Teams Immediately
Any security incident should be reported to your organization’s IT or cybersecurity department. They are professionals who can take the steps necessary to protect the organization. You should also report the threatening messages or profiles involved with the blackmail on Microsoft Teams. The platform administrators may respond and remove the account. This prevents the criminal from attacking others with the same scheme. Here is how to report blackmail on Microsoft Teams:
To Report Blackmail on Teams:
- Open the chat where the blackmail threats occurred.
- Click on the message or profile that you want to report.
- Select “Report a concern”.
- Select the reason that best fits your circumstances and submit the report.
Notify Law Enforcement
Reporting sextortion on Skype or other forms of blackmail to law enforcement was always recommended, and the same remains true for Microsoft Teams. The local authorities are an essential resource for blackmail victims. They can help you file a report, officially documenting the crime. Law enforcement officers can also conduct an investigation to uncover the perpetrator responsible. Furthermore, the authorities can help businesses recover lost data or funds.
Real-World Case: How “Email-Bombing” Leads to Ransomware
A ransomware cybercrime group is targeting businesses by exploiting Teams. They use multi-stage phishing tactics to gain a victim’s trust and access to their devices. Sophos reports that these criminals will “email bomb” victims’ business emails with thousands of spam emails. They will then simultaneously impersonate IT support and call the victim on Teams, leading them to assume that it’s about the sudden spike in spam emails.
After they get in touch with the victim, they manipulate them into providing remote access to their device. The criminal installs malware, disables security tools, and even encrypts critical files, which affects the entire organization.
Organizations Can Protect Themselves on Teams
Microsoft Teams How has become a go-to tool for many organizations. However, it’s always important to stay safe and secure, no matter the software. There are settings that can be used to strengthen cybersecurity on Teams and best practices that can reduce the risk of cyberattacks. Take note of the following steps:
- Review default settings on Teams. Organizations need to evaluate the default settings on Teams to ensure they are optimized for cybersecurity. Users can restrict or moderate external communication, limiting any form of malicious messages.
- Have a zero-trust mindset. Every user must have a small amount of skepticism toward any online interaction. Do your due diligence and verify senders before trusting them.
- Strengthen cybersecurity protocols. Things like two-factor authentication and improved endpoint monitoring can add an extra layer of protection from cyberattacks.
- Stay up to date on the latest cyberattacks. According to Mimecast, 95% of data breaches are caused by human error. Organizations need to keep their employees educated and aware of best security practices to reduce the risk of security incidents. The same is true for individuals. Staying educated about cybercrimes allows you to spot the warning signs of a scam early on. And if you want to continue learning about cybercrimes and security awareness, you can visit the Cyber Investigation Inc. blog for the latest insights and resources.







